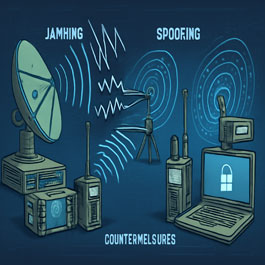
In today’s digital battlespace, Electronic Warfare (EW) has emerged as a pivotal force multiplier in modern military operations. No longer confined to traditional kinetic engagements, warfare now extends to the electromagnetic spectrum—a domain where signals are as crucial as soldiers, and disruption can be as powerful as destruction.
This article delves into the core concepts of EW, focusing on jamming, spoofing, and the countermeasures developed to defend against them.
What is Electronic Warfare (EW)?
Electronic Warfare is the use of the electromagnetic spectrum (EMS)—radio waves, infrared, microwave, and more—to detect, intercept, disrupt, deceive, or disable an enemy’s communications, navigation, and radar systems. EW is divided into three broad categories:
- Electronic Attack (EA) – using EMS to degrade, neutralize, or destroy enemy capabilities.
- Electronic Protection (EP) – safeguarding friendly systems against EW attacks.
- Electronic Support (ES) – detecting and identifying EMS signals to gain situational awareness.
Jamming: Disrupting the Signal
What is Jamming?
Jamming refers to intentionally transmitting radio signals to interfere with the reception of legitimate signals. The goal is to degrade or completely block communication, radar, or navigation systems.
Types of Jamming:
- Spot Jamming: Targets a single frequency.
- Barrage Jamming: Covers a range of frequencies simultaneously.
- Sweep Jamming: Rapidly shifts across multiple frequencies.
- Deceptive Jamming: Mimics legitimate signals to confuse receivers.
Real-World Applications:
Jamming is widely used to suppress enemy radars, GPS signals, and communication channels, often during aerial, naval, or ground operations. For instance, disrupting GPS during missile targeting can prevent accurate strikes.
Spoofing: Deceiving the Receiver
What is Spoofing?
Spoofing involves sending false or misleading signals to deceive a system. Instead of blocking a signal like jamming, spoofing tricks a receiver into accepting fake data as legitimate.
Common Targets:
- GPS Spoofing: Alters navigation data, redirecting vehicles or drones.
- Radar Spoofing: Creates ghost targets or hides real ones.
- Communication Spoofing: Sends false commands or disrupts coordination.
Notable Incidents:
One of the most cited spoofing events was the alleged hijacking of a U.S. drone in 2011, where GPS spoofing is believed to have led it astray. The technology is also a growing concern in cybersecurity and autonomous vehicles.
Countermeasures: Defending the Spectrum
1. Frequency Hopping Spread Spectrum (FHSS):
Changes frequencies in a synchronized pattern, making it harder for jammers to keep up.
2. Anti-Jam GPS (AJ-GPS):
Uses advanced filtering and directional antennas to resist jamming and spoofing.
3. Adaptive Filters & AI Algorithms:
Detect unusual patterns in signals to identify spoofing attempts in real time.
4. Encryption & Authentication:
Secure communication protocols ensure only legitimate signals are accepted.
5. Spectrum Monitoring & Management:
Real-time scanning helps identify EW threats and adjust frequencies dynamically.
The Future of EW: Smarter, Faster, Autonomous
As technology advances, EW systems are becoming more autonomous and AI-driven, capable of detecting and responding to threats without human intervention. Countries are investing heavily in next-generation EW systems that can operate in complex and contested environments like cyber-EW convergence, drone swarms, and space-based electronic warfare.
Conclusion
Electronic Warfare is a silent, invisible battleground—yet its outcomes can tip the scales of a conflict. From jamming enemy radars to spoofing navigation systems, EW offers both offensive and defensive capabilities that are integral to modern defense strategy. As threats evolve, so too must our understanding and innovation in this critical field.
Whether you’re a defense professional, a student, or a curious mind, understanding EW is essential to grasp how wars are fought—and won—in the 21st century.